
Conquering Data Challenges For Your Generative AI Success
Embarking on the journey of implementing successful Generative AI requires a strong and reliable foundation, with data preparation at its heart.
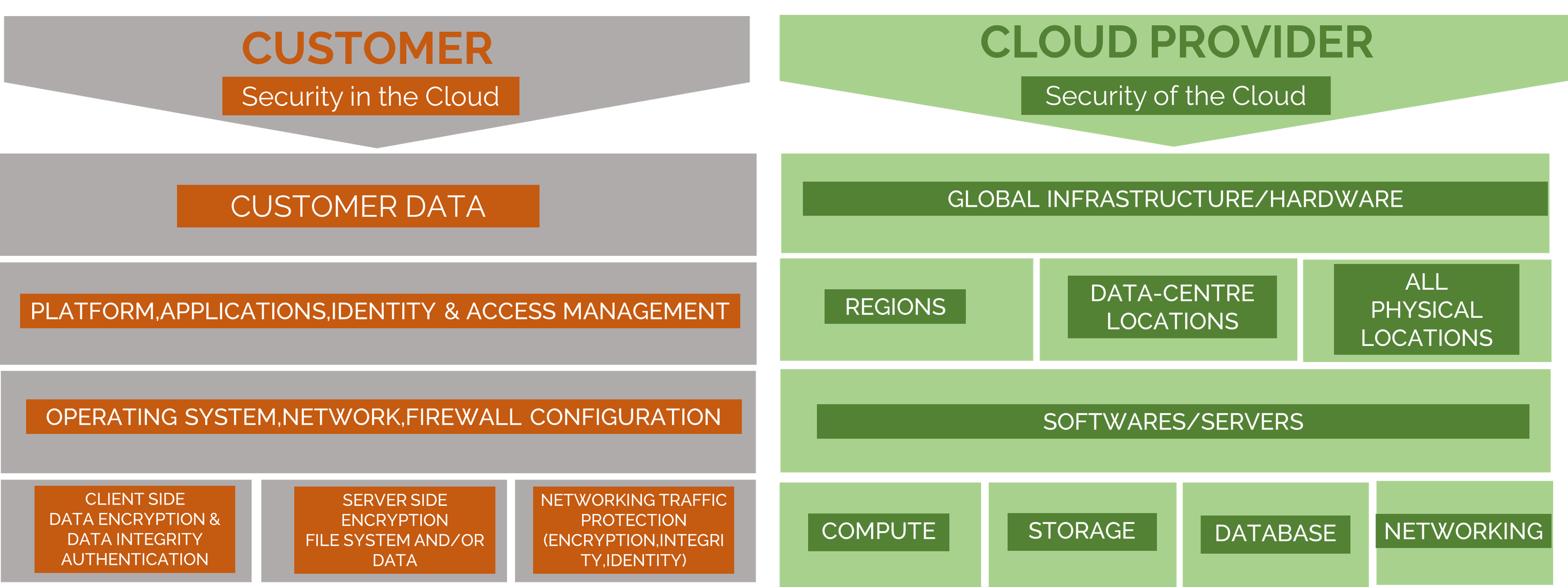
While Cloud providers stand firmly committed to providing the security, confidentiality, integrity, and transparency of the customer’s business-critical data, however, the security of the data, workloads & applications deployed in the Cloud is equally dependent upon the customers as well. The Cloud providers are responsible for the “Security of the Cloud“, while the customers are responsible for the “Security in the Cloud“.

The Cloud provider is responsible for the security of the Cloud, which means that it is responsible for all the security aspects of the Global infrastructure that offer the Cloud services. This infrastructure includes the software, hardware, and networking facilities. In addition to that, the Cloud provider is also responsible for the security configuration of its Managed-Services products – be it Servers, Databases, and OS configurations.
Broadly the key responsibility areas of the Cloud provider are :
Physical security of the Cloud infrastructure is maintained at the highest level, For example, AWS data-centers are hosted in nondescript facilities and the physical access is strictly controlled. The power supply into these facilities is fully redundant and equipped with 24|7 USP backups.
Any configuration changes to the Cloud infrastructure are performed under well-defined industry best practices and guidelines by the Cloud provider. These changes whether routine or emergency are well authorized, logged, tested, approved, and documented to be able to back-track every single activity point.
In Cloud, security is built in every single layer of the infrastructure. Each service that the Cloud service provider provides to its customer, is architected to work efficiently and securely with all the networks and the platforms. Service-level security is one of the core responsibilities of the Cloud service provider.
Cloud providers build and implement security tools to allow customers to automate routine tasks. This helps them to eliminate many human configuration errors and focus on high-priority areas. Customers leverage this security automation to become more agile and responsive, which makes it easy for them to create more secure Cloud solutions and deploy.
Customers are responsible for the “Security in the Cloud”. Just as they are responsible for the security of their on-premises data-centers, applications & tools, similarly in Cloud they have equal or rather higher liberty and controls over the security of their systems running in the Cloud. Customers continue to retain the ownership of their intellectual property running in the Cloud.
The customer has the flexibility to choose the geographical region to host their data and applications. These data & applications can be easily configured to be replicated by the customers with their choice of regions across the globe. In addition to this, the customer can and must choose the type of data-encryption they want to apply to their applications in the Cloud. Cloud providers like AWS provide their customers the encryption options so that they can configure the content to either use Data-in-transit-encryption or Data-at-rest-encryption or both. The ownership of the encryption keys completely lies with the customers and it can be used to implement additional security controls to protect their content.
Just as in the case of on-premises, customers continue to perform all the necessary security configuration and management tasks on their Cloud Infrastructure Services (IaaS) too. This includes applying any updates on the security patches or configuring all the security firewall settings. As the responsibility of operating the IT environment in the Cloud is shared between the Cloud provider and its customers, similarly the management, operation, and verification of the Cloud IT environment are also shared between both the stakeholders.
In addition to the security provided by the Cloud provider, customers can access hundreds of industry-leading products, which can integrate with existing controls in the customer’s on-premises environments, for example, Symantec, Splunk, Alert Logic & many more. These products complement the existing Cloud services to enable the customers to deploy a comprehensive security architecture and a more seamless experience across cloud and on-premises data-centers.
Lastly, compliance and regulations are critical parameters to maintain the “Security in/of the Cloud”. There are many compliance programs available globally and the whole purpose of their existence is to ensure customer data privacy and protection. They help the Customers and Cloud service providers to diligently implement the industry best-practices, security frameworks, data privacy laws & regulations. Some of these compliance programs are industry and vertical-specific while others operate in certain geographies. For example CSA(Cloud Security Alliance), ISO 27017(Cloud specific controls), ISO 27018(Personal Data Protection), PCI DSS level1(Payment Card Standa
rds), HIPAA(Protected health, Information), FISMA(Federal Information Security Management), and SOC1, SOC2, SOC3 ( System and Organization Control ) are a few of them.
Build your secure IT infrastructure on a subscription based model and avoid large expenditures and control your IT cost.. Know More...

Embarking on the journey of implementing successful Generative AI requires a strong and reliable foundation, with data preparation at its heart.

No AI strategy can thrive or endure without high-quality data because data is the lifeblood that fuels generative AI…
Amazon Athena lets you query data where it lives without moving, loading, or migrating it. You can query the data from relational, non-relational…
Amazon Redshift is a cloud-based next-generation data warehouse solution that enables real-time analytics for operational databases, data lakes….
Navigating New Horizons With Gen AI Stay At The Forefront of AI-driven Innovation We excel in developing custom generative AI applications that seamlessly integrate with
Cloud Cost Optimization Have A Greater Control Over Your IT Spending A well-defined Cloud Cost Optimization Strategy can help you to implement the cloud best
Data Lake Solutions Establish a Central Data Lake for Your Data Management Needs Unlock the full potential of your data by leveraging our comprehensive data
Accelerate your Digital Transformation Find The Right Way Forward with Cloud Proof of Concepts(POC) Rapid Solution Prototyping Allows You To Minimize Any Unforeseen Risks and
